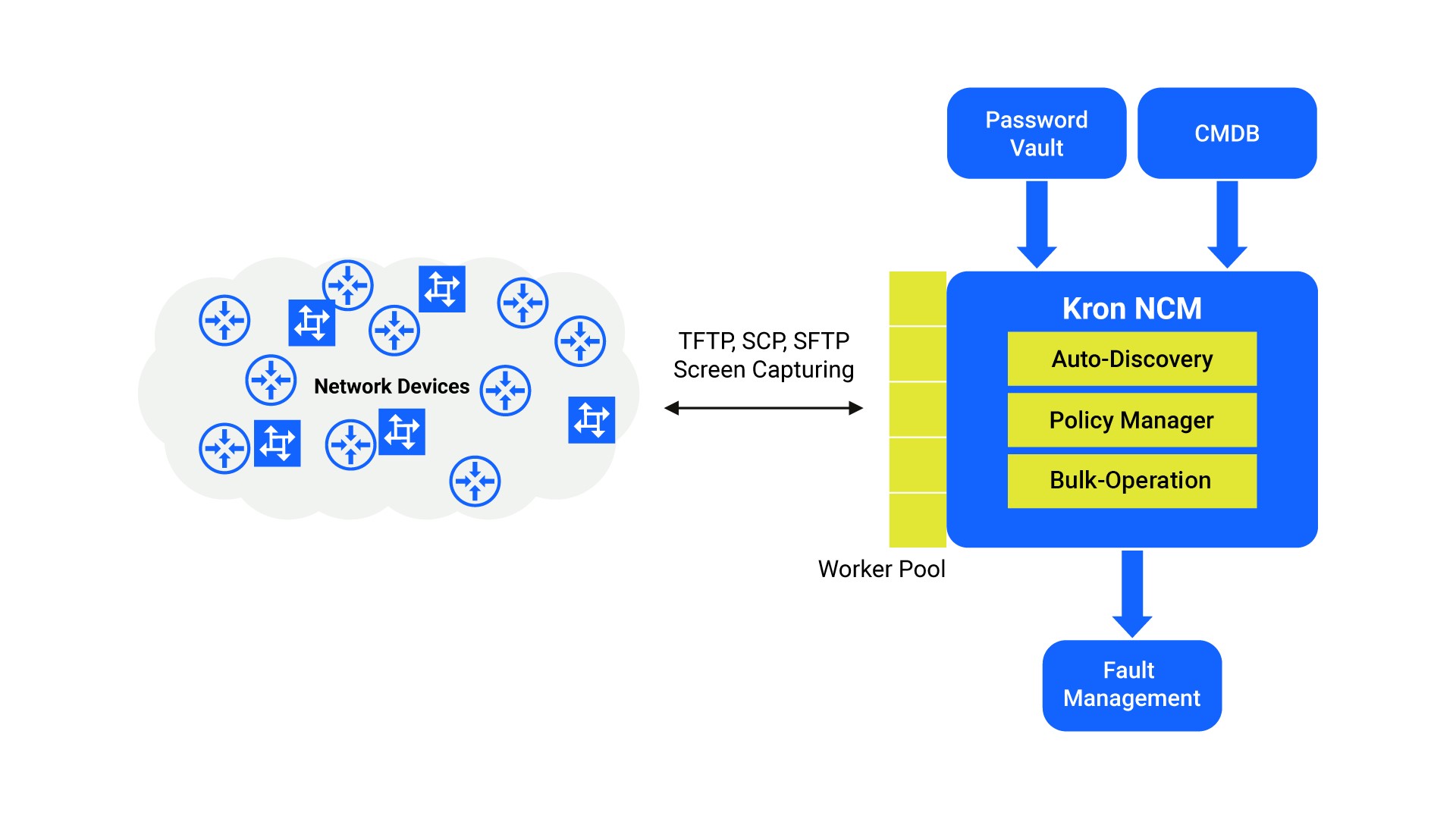
How Kron's NCM Works?
Kron’s NCM runs commands on network devices through SSH and telnet protocols for task automations and configuration backups. It receives backups through sftp, tftp and scp file transfer protocols or with screen capturing technologies, and if the backup differs from the previous version Kron’s NCM mirrors the new configuration to save it as encrypted. Every time a configuration is backed up, Kron’s NCM automatically runs a compliance check on new configurations and alerts you if there are any changes or any uncompliant line is identified. Moreover, remediation scripts can be defined to be activated when an uncompliant scenario is detected.